Sigma Rules List 1 to 100
Sigma is a standardized rule syntax which can be converted into many different SIEM-supported syntax formats. The Recorded Future Platform allows clients to access and download Sigma rules developed by Insikt Group for use in their organizations. Sigma Rules List PDF can be download from the link given at the bottom of this page.
The Sigma rules provided by the open-source Sigma project and the custom rules developed by Recorded Future (available to existing clients only) offer a powerful capability to detect and respond to credential harvesting using existing SIEM solutions. When combined with properly configured host-based logging, using tools such as Sysmon, Sigma rules can elevate the ability of an organization to detect and respond to threats with increased accuracy and efficiency.
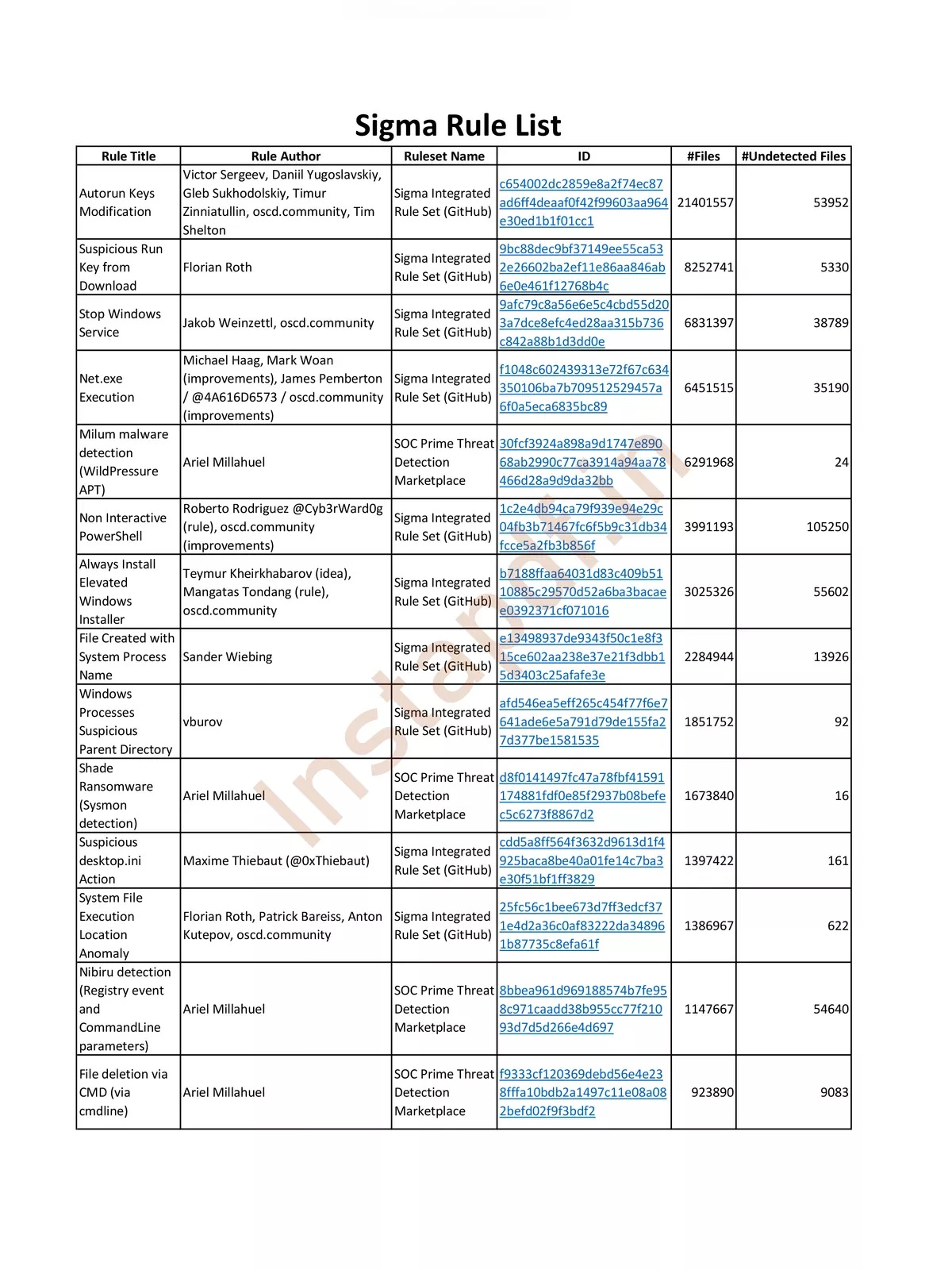
Sigma Rules List
| Rule Title | Rule Author | Ruleset Name | ID | Files | Undetected Files |
|---|---|---|---|---|---|
| Autorun Keys Modification | Victor Sergeev, Daniil Yugoslavskiy, Gleb Sukhodolskiy, Timur Zinniatullin, oscd.community, Tim Shelton | Sigma Integrated Rule Set (GitHub) | c654002dc2859e8a2f74ec87ad6ff4deaaf0f42f99603aa964e30ed1b1f01cc1 | 21401557 | 53952 |
| Suspicious Run Key from Download | Florian Roth | Sigma Integrated Rule Set (GitHub) | 9bc88dec9bf37149ee55ca532e26602ba2ef11e86aa846ab6e0e461f12768b4c | 8252741 | 5330 |
| Stop Windows Service | Jakob Weinzettl, oscd.community | Sigma Integrated Rule Set (GitHub) | 9afc79c8a56e6e5c4cbd55d203a7dce8efc4ed28aa315b736c842a88b1d3dd0e | 6831397 | 38789 |
| Net.exe Execution | Michael Haag, Mark Woan (improvements), James Pemberton / @4A616D6573 / oscd.community (improvements) | Sigma Integrated Rule Set (GitHub) | f1048c602439313e72f67c634350106ba7b709512529457a6f0a5eca6835bc89 | 6451515 | 35190 |
| Milum malware detection (WildPressure APT) | Ariel Millahuel | SOC Prime Threat Detection Marketplace | 30fcf3924a898a9d1747e89068ab2990c77ca3914a94aa78466d28a9d9da32bb | 6291968 | 24 |
| Non Interactive PowerShell | Roberto Rodriguez @Cyb3rWard0g (rule), oscd.community (improvements) | Sigma Integrated Rule Set (GitHub) | 1c2e4db94ca79f939e94e29c04fb3b71467fc6f5b9c31db34fcce5a2fb3b856f | 3991193 | 105250 |
| Always Install Elevated Windows Installer | Teymur Kheirkhabarov (idea), Mangatas Tondang (rule), oscd.community | Sigma Integrated Rule Set (GitHub) | b7188ffaa64031d83c409b5110885c29570d52a6ba3bacaee0392371cf071016 | 3025326 | 55602 |
| File Created with System Process Name | Sander Wiebing | Sigma Integrated Rule Set (GitHub) | e13498937de9343f50c1e8f315ce602aa238e37e21f3dbb15d3403c25afafe3e | 2284944 | 13926 |
| Windows Processes Suspicious Parent Directory | vburov | Sigma Integrated Rule Set (GitHub) | afd546ea5eff265c454f77f6e7641ade6e5a791d79de155fa27d377be1581535 | 1851752 | 92 |
| Shade Ransomware (Sysmon detection) | Ariel Millahuel | SOC Prime Threat Detection Marketplace | d8f0141497fc47a78fbf41591174881fdf0e85f2937b08befec5c6273f8867d2 | 1673840 | 16 |
| Suspicious desktop.ini Action | Maxime Thiebaut (@0xThiebaut) | Sigma Integrated Rule Set (GitHub) | cdd5a8ff564f3632d9613d1f4925baca8be40a01fe14c7ba3e30f51bf1ff3829 | 1397422 | 161 |
| System File Execution Location Anomaly | Florian Roth, Patrick Bareiss, Anton Kutepov, oscd.community | Sigma Integrated Rule Set (GitHub) | 25fc56c1bee673d7ff3edcf371e4d2a36c0af83222da348961b87735c8efa61f | 1386967 | 622 |
| Nibiru detection (Registry event and CommandLine parameters) | Ariel Millahuel | SOC Prime Threat Detection Marketplace | 8bbea961d969188574b7fe958c971caadd38b955cc77f21093d7d5d266e4d697 | 1147667 | 54640 |
| File deletion via CMD (via cmdline) | Ariel Millahuel | SOC Prime Threat Detection Marketplace | f9333cf120369debd56e4e238fffa10bdb2a1497c11e08a082befd02f9f3bdf2 | 923890 | 9083 |
| Suspicious Svchost Process | Florian Roth | Sigma Integrated Rule Set (GitHub) | a0daa529834b3c5230b4524da005a6b6503e7cb061e298a8f74e0dc1fee0a008 | 845991 | 133 |
| Windows PowerShell Web Request | James Pemberton / @4A616D6573 | Sigma Integrated Rule Set (GitHub) | 2637f98feb69311f94822998eb3c8b8d217e6c5767e071536ca54f9da830e236 | 805020 | 104 |
| Execution from Suspicious Folder | Florian Roth | Sigma Integrated Rule Set (GitHub) | f8d48ec1128b00975e61e06393f6bb04a1d033a94c556d213b3bcb78a80589d8 | 643979 | 5419 |
| Suspect Svchost Activity | David Burkett | Sigma Integrated Rule Set (GitHub) | dc04e64e69f5446c2a31920ee22415626307d5f3d0fb73ad81b9d3301a41000a | 568031 | 87 |
| Direct Autorun Keys Modification | Victor Sergeev, Daniil Yugoslavskiy, oscd.community | Sigma Integrated Rule Set (GitHub) | b5f76af9d8101930af8d4fee71f3a5395b47eff6bb88e581db02bf890242d79b | 549037 | 130 |
| CSRSS.exe spawned from unusual location (possible mimicking) (via cmdline) | SOC Prime Team | SOC Prime Threat Detection Marketplace | c3e407003db6c8b95e5a7dcbea08bddf8b53b265400c2feb32abfa523336257c | 531710 | 11 |
| Swisyn Trojan (Sysmon detection) | Ariel Millahuel | SOC Prime Threat Detection Marketplace | 173f49a095aef2bc0480b5f8a8ae6c2d0e4125f9096d618a3865346b34d726fa | 494316 | 108 |
| Suspicious Program Location with Network Connections | Florian Roth | Sigma Integrated Rule Set (GitHub) | 01b1cc2515aec2562e5e8cd3c88a60677a1acd2d680b289cf67fa493abe433d2 | 482076 | 5335 |
| Scheduled Task Creation | Florian Roth | Sigma Integrated Rule Set (GitHub) | 3bc9d14114a6b67367a24df21134d0564d6f08a0ad903d68f9b25e9d8b7f0790 | 431585 | 473 |
| Startup Folder File Write | Roberto Rodriguez (Cyb3rWard0g), OTR (Open Threat Research) | Sigma Integrated Rule Set (GitHub) | 56b8c79acb8e444c2b00be5c9d3cb8e33e863ccb3506d635f907a49cd053c84f | 323029 | 118 |
| Executables Started in Suspicious Folder | Florian Roth | Sigma Integrated Rule Set (GitHub) | 934747e347848f3bf5d2222f0c29c4c6e42831b94a6e0ce77ff40017e5f11fd2 | 318156 | 2408 |
| Suspicious Program Location Process Starts | Florian Roth | Sigma Integrated Rule Set (GitHub) | c593fd1eac248d2f05a155e6c8ef2682b9022a12bc03104ff8e9e7c40f585268 | 315071 | 2406 |
| Execution File Type Other Than .exe | Max Altgelt | Sigma Integrated Rule Set (GitHub) | 2104d1ee1ce64e7aa3dbd368652a54ce160e6a5751019af14601fc8fd1df8086 | 314199 | 3369 |
| Possible Applocker Bypass | juju4 | Sigma Integrated Rule Set (GitHub) | b9996fdb64c94bd97526744b8287a3b3b02ac4eceff0980c672209adae0be6e5 | 264915 | 225 |
Sigma Rules List
You can download the Sigma Rules List PDF using the link given below.